.
Other Virus Aliases
W32/Infector.Gen2 (Avira)
- Win32/Ramnit.A (CA) Win32/Ramnit.AY (ESET),Win32/Ramnit.F (Eset),Win32.Rmnet (Dr.Web), W32.Infector (Ikarus), W32/Ramnit.a (McAfee), W32/Patched-I (Sophos), PE_RAMNIT.A (Trend Micro),Type_Win32 (Kaspersky), Win32/Zbot.A (AVG)
Virus execution
When executed, the virus copies itself in some of the the following locations
- %programfiles%MicrosoftWaterMark.exe
- %commonprogramfiles%MicrosoftWaterMark.exe
- %appdata%MicrosoftWaterMark.exe
- %system%MicrosoftWaterMark.exe
- %windir%MicrosoftWaterMark.exe
- %temp%MicrosoftWaterMark.exe
- %homedrive%%homepath%MicrosoftWaterMark.exe
The following Registry entries are set:
- [HKEY_LOCAL_MACHINESoftwareMicrosoftWindows NTCurrentVersionWinlogon]
- “Userinit” = “%originalvalue%, %malwarefolder%MicrosoftWaterMark.exe”
This causes the virus to be executed on every system start.
The virus creates and runs a new thread with its own program code within the following processes:
- Svchost.exe
- Executable file infection
- The virus searches local drives for files with the following file extensions:
- .exe
- .dll
It avoids files which contain any of the following strings in their path:
- RMNetwork
- Files are infected by adding a new section that contains the virus .
The host file is modified in a way that causes the virus to be executed prior to running the original code. The size of the inserted code is 53 KB .
Virus File infection
- The virus searches local drives for files with the following file extensions:
- .htm
- .html
The Windows Shell allows local users or remote attackers to execute arbitrary code via a crafted *.lnk, *.pif shortcut file when its icon is displayed.
No further user interaction is required to execute arbitrary code.
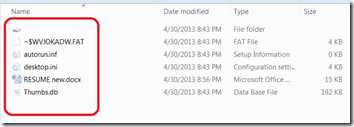
The virus creates the following files:
- %removabledrive%RECYCLERS-7-1-36-6133081425-6700277004-675130086-4217%variable1%.exe
- %removabledrive%RECYCLERS-7-1-36-6133081425-6700277004-675130086-4217%variable2%.cpl
- %removabledrive%autorun.inf
- %removabledrive%Copy of Shortcut to (1).lnk
- %removabledrive%Copy of Shortcut to (2).lnk
- %removabledrive%Copy of Shortcut to (3).lnk
- %removabledrive%Copy of Shortcut to (4).lnk
The virus acquires data and commands from a remote computer or the Internet.
The virus contains a list of addresses.
It can execute the following operations:
- capture screenshots
- send gathered information
- download files from a remote computer and/or the Internet
- run executable files
- shut down/restart the computer
The virus may create the following files:
- %system%dmlconf.dat
The virus connects to the following addresses:
- google.com
- bing.com
- yahoo.com
The virus may create and run a new thread with its own program code within any running process.
The Virus Removal
To fix the issue:
- update the anti-virus into it’s latest signature
- Then run a quick scan in your computer
- Run infected external storage
After the Win32 Ramnit worm virus removed. Follow the steps below to completely restore your external drive way back before the problem occured.
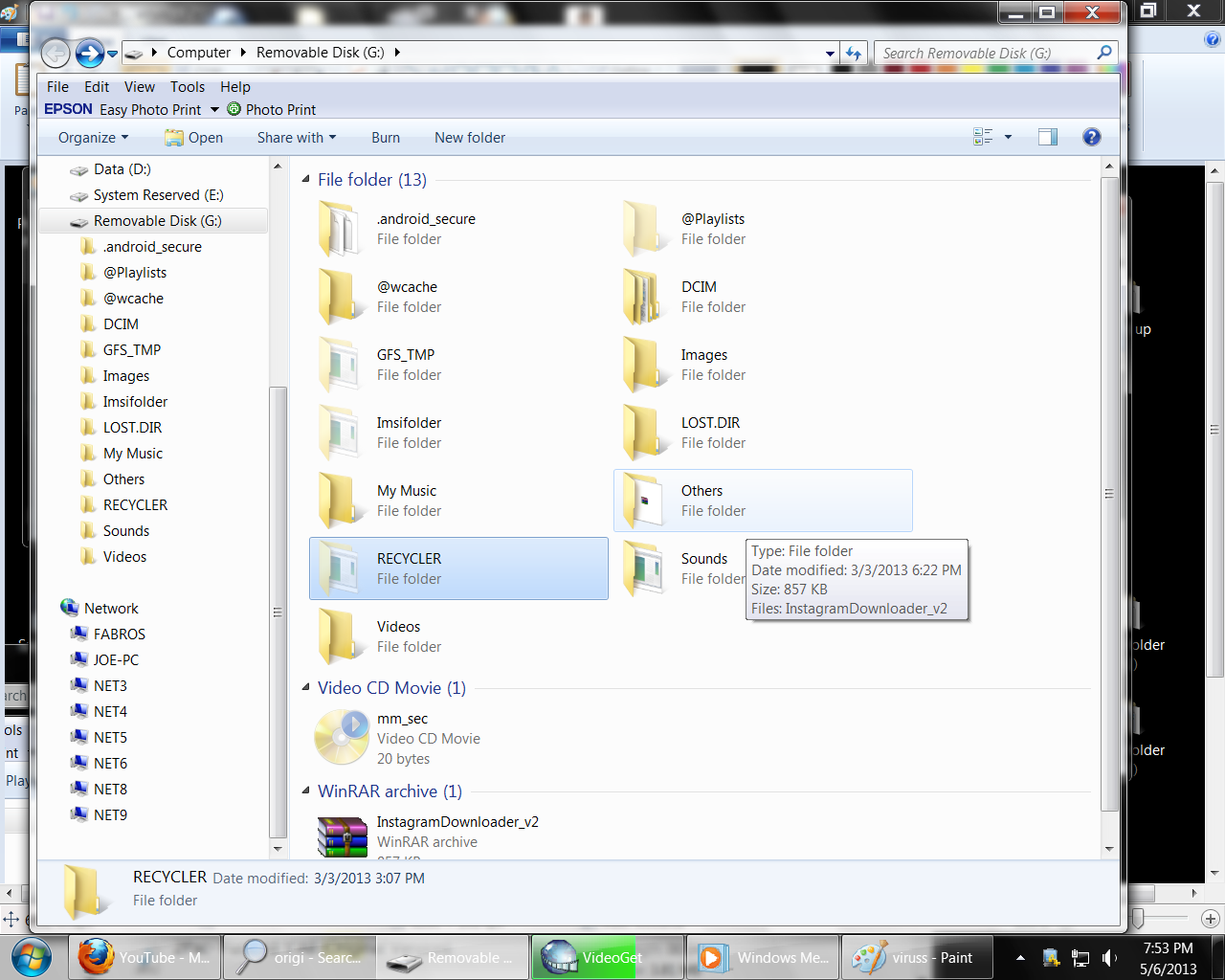
- Open the external drive
- Delete all files except the drive icon that have no drive letter
- Open the drive icon with no drive letter
- Select all your files and cut or copy
- Then go back to my computer
- Open external storage device (that is, flash drive, usb drive, external hard disk or whatever it is)
- Paste your file
- Then, delete the “the drive icon that have no drive letter”
Before you proceed make sure the following Folder Options Menu are selected:
- Select Show hidden files, folders, or drives
- Uncheck Hide extensions for known file types
- Unchecked Hide protected operating files (recommended)